
Ron Amadeo
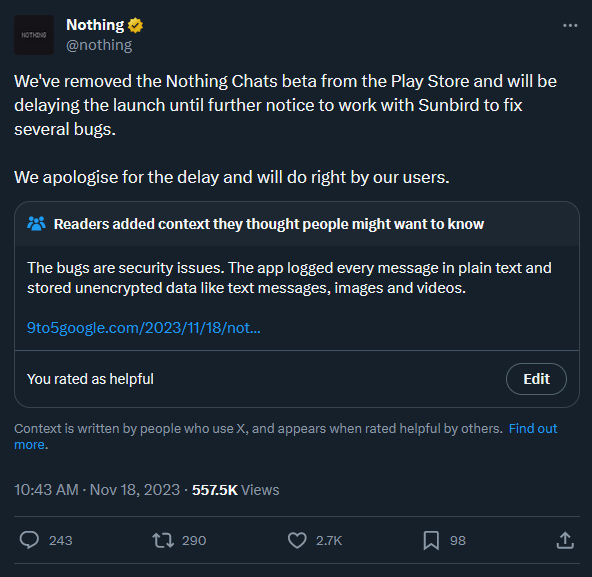
It turns out that companies that obstruct the media’s security questions aren’t actually that good at security. Last Tuesday, Nothing Chats — a chat app from Android maker Nothing and app startup Sunbird — claimed to be able to hack Apple’s iMessage protocol and give Android users blue bubbles. We immediately flagged Sunbird as a company that made empty promises for about a year and seemed negligent when it came to security. The app launched on Friday anyway and was immediately torn apart by the internet due to numerous security issues. It didn’t take 24 hours before Nothing pulled the app from the Play Store on Saturday morning. Sunbird, of which Nothing Chat is just a redesign, has also been “paused.”
The initial sales pitch for this app — that it would log you into iMessage on Android if you handed over your Apple username and password — was a huge security red flag that meant Sunbird would need a highly secure infrastructure to avoid disaster. Instead, the app turned out to be not as secure as it could be. Here’s the nothing statement:
None The chat has been closed.
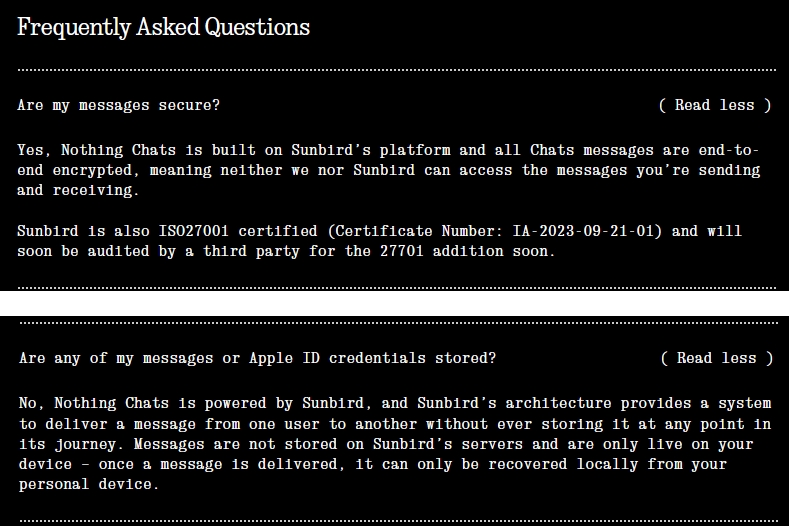
How bad are the security issues? both of them 9to5Google And Text.com (Which he owns automatic, the company behind WordPress) has revealed very poor security practices. Not only was the app not end-to-end encrypted, as Nothing and Sunbird claimed multiple times, but Sunbird actually logged the messages and stored them in plain text in both bug reporting programs sentry And In the Firebase store. The authentication tokens are sent over unencrypted HTTP so this token can be intercepted and used to read your messages.
Text.com’s investigation revealed a pile of vulnerabilities. The blog says: “When a user receives a message or attachment, it is not encrypted on the server side until the client sends a request to acknowledge it and delete it from the database. This means that an attacker subscribed to the Firebase Realtime DB will always be able to access the messages before or at the moment Read by the user.” Text.com was able to intercept the authentication code sent over unencrypted HTTP and subscribe to changes occurring in the database. This means live updates of “incoming and outgoing messages, account changes, etc.” not only from themselves, but from other users as well.
Text.com released a Proof of concept The application that can fetch your supposedly end-to-end encrypted messages from Sunbird servers. Batuhan Ikuz, a product engineer at Text.com, has also released a tool that will delete some of your data from Sunbird’s servers. Içöz recommends that any Sunbird/Nothing Chat users change their Apple IDs now, cancel their Sunbird session, and “assume that your data has already been compromised.”
9to5Google Dylan Russell I looked into the app and found that, in addition to all public text data, “all documents (photos, videos, audios, pdfs, vCards…) sent through Nothing Chat and Sunbird are public.” Russell found that 630,000 media files are currently stored by Sunbird, and it appears he can access some of them. The Sunbird app suggested users transfer vCards — virtual business cards filled with contact information — and Russell says the personal information of more than 2,300 users could be accessed. Russell calls the whole fiasco “probably the biggest privacy nightmare I’ve seen from a phone manufacturer in years.”
Nothing promises security, which has not been incredibly taken down.
Despite being the cause of this massive disaster, Sunbird had been strangely calm during this whole mess. The app’s X (formerly Twitter) page still says nothing about shutting down Nothing Chats or Sunbird. This is probably for the best because some of Sunbird’s early responses to the security concerns raised on Friday don’t appear to have come from a competent developer. In the beginning, the company Defend its use Unencrypted HTTP for some web transactions, Text.com’s Bajaria told “HTTP is only used as part of the initial one-time request from the app to inform the back-end of the next iMessage connection frequency that will follow over a separate communication channel. From the beginning, Sunbird focused on security.“Text.com’s investigation explained that this was a ‘load-balanced Express server that did not implement SSL, so an attacker could easily intercept requests.'” This use of HTTP allowed Text.com to intercept authentication tokens.
Modern security best practices say that it is never acceptable to use unencrypted HTTP for any online transaction, and many platforms completely block plaintext HTTP transmissions by default. Chrome displays a full-page warning when trying to access an HTTP page and prompts the user to click on a warning message. Android Disable clear text traffic by default and needs a developer to run a special flag so that the request can pass through. Projects like Let’s Encrypt have not only made using HTTPS easy and free, but actually so Easier To encrypt everything because you don’t have to deal with all the security barriers. These are the basics of 2023 internet use, and seeing any developer argue against them is shocking, especially when that developer also wants to be trusted with your Apple account. It would be different if this was a huge mistake, but Sunbird thought it was okay!
There hasn’t always seemed like an Android manufacturer that was more hype than substance, but now we can add the word “sloppy” to that list. The company joined forces with Sunbird, redesigned its app, and created a portfolio Promotional website And YouTube videoAnd he coordinated a media statement with Famous YouTubersAll without doing the slightest due diligence on Sunbird’s apps or security claims. It’s unbelievable that these two companies could have gotten this far, as launching Nothing Chats required a systemic security failure across two entire companies.
Nothing claims that the app will come back once Sunbird “fixes several bugs.” When your entire application was built with seemingly no concern about security, I don’t see how you can fix that in a week or two. If Nothing Chats returns to the Play Store, will anyone still trust it enough to enter their credentials?

“Web specialist. Lifelong zombie maven. Coffee ninja. Hipster-friendly analyst.”


:no_upscale()/cdn.vox-cdn.com/uploads/chorus_image/image/72661014/nitrodecklead.0.jpg)